Practical Malware Analysis - Lab 1 write-up

Practical Malware Analysis is a book that is often recommended by people that perform malware analysis. I’ve recently started reading this book and it’s been a really fun and informative read so far. In this series I’ll be sharing my write-ups for the labs included in this book. There’s a total of 18 chapters that contain lab exercises. Let’s kick it off with the labs included in chapter 1!
Lab 1-1
This lab uses the files Lab01-01.exe and Lab01-01.dll. Use the tools and techniques described in the chapter to gain information about the files and answer the questions below.
1. Upload the files to http://www.VirusTotal.com/ and view the reports. Does
either file match any existing antivirus signatures?
Answer: Lab01-01.dll (SHA256: f50e42c8dfaab649bde0398867e930b86c2a599e8db83b8260393082268f2dba)
is detected by 44 out of 70 security vendors as malicious at the time of writing.
Lab01-01.exe (SHA256:
58898bd42c5bd3bf9b1389f0eee5b39cd59180e8370eb9ea838a0b327bd6fe47) is detected by 53 out of 71 security vendors as malicious at the time of writing.
2. When were these files compiled?
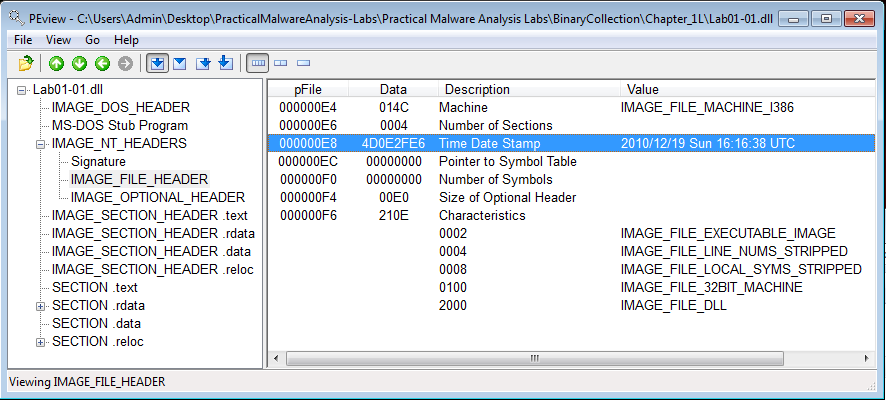
Answer: To determine when the files were compiled, we can look at the IMAGE_FILE_HEADER entry in a tool like PEview.
Lab01-01.dll was compiled on 19 December 2010 at 16:16:38 UTC.
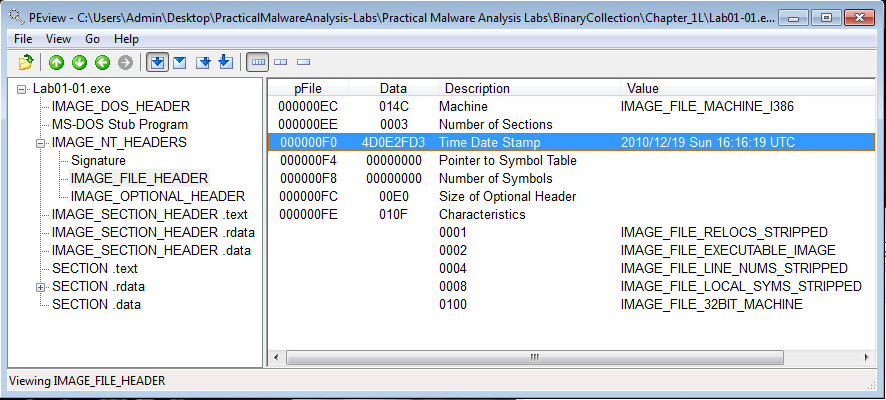
Lab01-01.exe was compiled on 19 December 2010 at 16:16:19 UTC.
3. Are there any indications that either of these files is packed or obfuscated? If so, what are these indicators?
Answer: For this question, I first compared the Virtual Size to the Size of Raw Data of the PE file section headers. Virtual Size tells us how much space is allocated for a section during the loading process. Size of Raw Data tells us how big the section is on disk.
These two values should usually be equal, because data should take up just as much space on the disk as it does in memory (small differences are normal, and are due to differences between alignment in memory and on disk). If the Virtual Size is much larger than the Size of Raw Data, you know that the section takes up more space in memory than it does on disk. This is often indicative of packed code, particularly if the .text section is larger in memory than on disk.
- Lab01-01.dll
.textsection- Virtual Size: 039E
- Size of Raw Data: 1000
- Lab01-01.dll
.rdatasection- Virtual Size: 23FC6
- Size of Raw Data: 24000
- Lab01-01.dll
.datasection- Virtual Size: 006C
- Size of Raw Data: 1000
- Lab01-01.dll
.relocsection- Virtual Size: 0204
- Size of Raw Data: 1000
- Lab01-01.exe
.textsection- Virtual Size: 0970
- Size of Raw Data: 1000
- Lab01-01.exe
.rdatasection- Virtual Size: 02B2
- Size of Raw Data: 1000
- Lab01-01.exe
.datasection- Virtual Size: 00FC
- Size of Raw Data: 1000
We can see that the Virtual Size of the sections is never larger than the Size of Raw Data.
Packed and obfuscated code will often include at least the functions LoadLibrary and GetProcAddress, which are used to load and gain access to additional functions (LdrGetProcAddress and LdrLoadDll could also be used). If we take a look at the import information of Lab01-01.dll and Lab01-01.exe, we can see that these functions are not used.
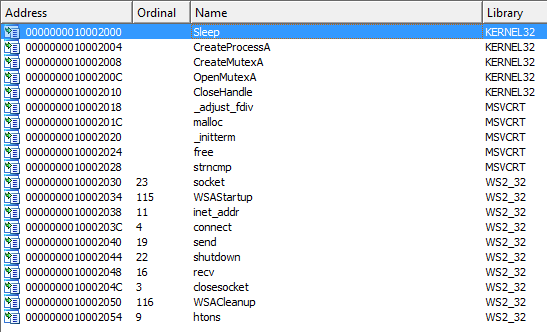
Figure: Import information of Lab01-01.dll
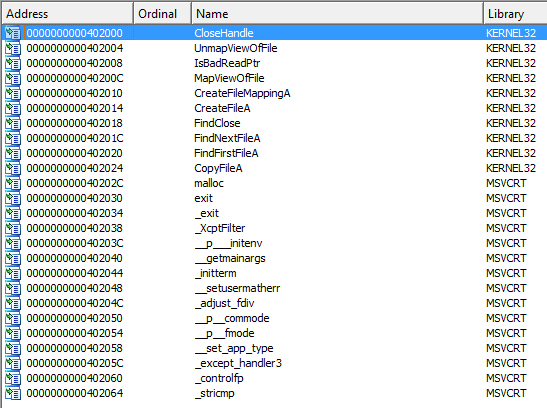
Figure: Import information of Lab01-01.exe
With this information available, I would say that the files are not packed or obfuscated.
4. Do any imports hint at what this malware does? If so, which imports are they?
Answer: Lab01-01.dll imports KERNEL32.dll, WS2_32.dll and MSVCRT.dll.
KERNEL32.dll is a very common DLL that contains core functionality, such ass access and manipulation of memory, files and hardware. 5 different functions of KERNEL32.dll are used by Lab01-01.dll: Sleep, CreateProcessA, CreateMutexA, OpenMutexA, CloseHandle.
WS2_32.dll is a networking DLL, indicating that the program likely connects to a network or performs network-related tasks. 10 different functions of WS2_32.dll are used by Lab01-01.dll: socket, WSAStartup, inet_addr, connect, send, shutdown, recv, closesocket, WSACleanup, htons.
MSVCRT.dll is the C standard libray for the Visual C++ (MSVC) compiler from version 4.2 to 6.0. It provides programs with most of the standard C library functions, such as string manipulation and memory allocation. 5 different functions of MSVCRT.dll are used by Lab01-01.dll, which I have not included here as I did not find them to be interesting.
Lab01-01.exe imports KERNEL32.dll and MSVCRT.dll. These libraries have already been described above. 10 different functions of KERNEL32.dll are used by Lab01-01.exe: CloseHandle, UnmapViewOfFile, IsBadReadPtr, MapViewOfFile, CreateFileMappingA, CreateFileA, FindClose, FindNextFileA, FindFirstFileA, CopyFileA. 15 different functions of MSVCRT.dll are used by Lab01-01.exe, which I have not included here as I did not find them to be interesting.
Based on the imports, I would guess that this malware finds and steals files by copying them from the victim computer (FindFirstFileA, FindNextFileA, and CopyFileA functions of KERNEL32.dll in Lab01-01.exe) and sending them over a network socket (all functions of WS2_32.dll in Lab01-01.dll). After reading the Reversing Malware Command and Control: From Sockets to COM post by Mandiant, I assume that it is most likely using a TCP session because the connect function is being called.
The malware also creates a mutex (CreateMutexA and OpenMutexA functions of KERNEL32.dll in Lab01-01.dll) to ensure that only one single instance of the malware is actually running.
5. Are there any other files or host-based indicators that you could look for on infected systems?
Answer: With the information collected so far, I believe that the following host-based indicator could be looked for:
- Value of the mutex that is being created
6. What network-based indicators could be used to find this malware on infected machines?
Answer: With the information collected so far, I believe that the following network-based indicator could be used:
- The IP address that is being used by the network socket (
127.26.152.13)
7. What would you guess is the purpose of these files?
Answer: The executable is being used to load the DLL file.
Comparing my answers to the Lab 1-1 solutions
Conclusions after comparison:
- I was on the right track with my guess that this malware finds and steals files by copying them. FindFirstFileA, FindNextFileA, and CopyFileA were indeed the most interesting functions in Lab01-01.exe. However, at this moment we can only state that it searches for and copies files. We cannot be sure that it sends these files over the network socket.
- The most interesting imports from Lab01-01.dll are CreateProcess and Sleep. These functions are commonly used as backdoors.
- If we look at the strings used by the malware, we can see a
C:\Windows\System32\kerne132.dllstring (note the number 1 instead of the letter l). This file could be used as a host indicator to search for the malware. - All of the imports from msvcrt.dll are functions that are included in nearly every executable as part of the wrapper code added by the compiler.
- This malware is complex, and will be returned to in lab 7-3 when the skills have been acquired to fully analyze it.
Lab 1-2
Analyze the file Lab01-02.exe.
1. Upload the Lab01-02.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
Answer: Lab01-02.exe (SHA256:
c876a332d7dd8da331cb8eee7ab7bf32752834d4b2b54eaa362674a2a48f64a6) is detected by 57 out of 71 security vendors as malicious at the time of writing.
2. Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
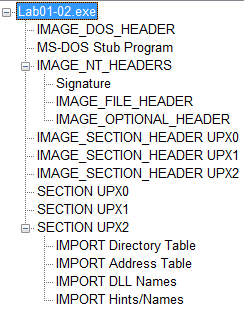
Answer: If we load the file into PEview, we can see that the section names are obfuscated. Instead of seeing section names such as .text and .rdata, we see UPX0, UPX1, and UPX2:
Let’s have a look at the Size of Raw Data and Virtual Size of these section headers.
- Lab01-02.exe
.UPX0section- Virtual Size: 4000
- Size of Raw Data: 0000
- Lab01-02.exe
.UPX1section- Virtual Size: 1000
- Size of Raw Data: 0600
- Lab01-02.exe
.UPX2section- Virtual Size: 1000
- Size of Raw Data: 0200
For all of the sections, the Virtual Size is larger than the Size of Raw Data. This indicates that the file is packed.
To confirm that this file is indeed packed, we can also look at the import information. As mentioned before, packed and obfuscated code will often include at least the functions LoadLibrary and GetProcAddress, which are used to load and gain access to additional functions (LdrGetProcAddress and LdrLoadDll could also be used).
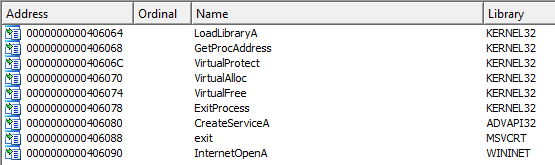
Figure: Import information of Lab01-02.exe
In the import information of Lab01-02.exe we can see that the LoadLibraryA and GetProcAddress functions of KERNEL32.dll are used.
With all of this information available, it is safe to say that the program is packed with UPX. UPX stands for Ultimate Packer for eXecutables, and is a free and open-source executable packer. UPX is a relatively simple and well-documented packer. We could easily unpack our sample by dowloading UPX and running it with upx -d. However, after reading that the UPX tool would not work if the packed binary would be memory injected in a later stage of the malware, I figured it would be good to practice manual unpacking instead. I followed along the How to unpack UPX packed malware with a SINGLE breakpoint write-up by Saket Upadhyay to unpack the sample.
First, we’re going to load our Lab01-02.exe sample in a debugger on our dynamic analysis VM. I will be using x32dbg for this.
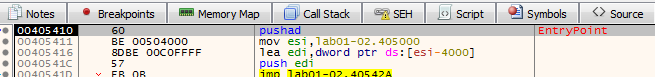
Once the sample is loaded, we press F9 to run to the EntryPoint of our binary: pushad. The pushad instruction pushes the contents of the general-purpose registers onto the stack.
During execution, binaries packed with UPX perform the following steps:
- Save all register states with pushad
- Unpack all sections in memory
- Dynamically resolve IAT (Import Address Table)
- Restore register states with popad
- Jump to OEP (Original Entry Point) and execute main code
In order to obtain an unpacked version of the sample, we will first search for the popad instruction:
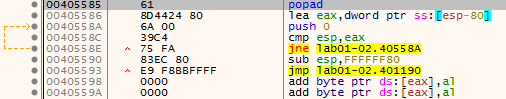
Now that we’ve located the popad instruction, we have to place a breakpoint at the first jmp instruction that immediately comes after popad. In this case, we will place a breakpoint at the address 00405593.
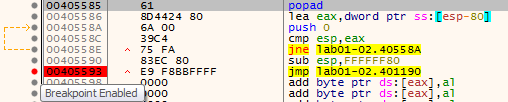
With our breakpoint set, let’s run to user code again by pressing F9 in order to hit the jump.
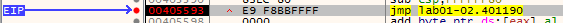
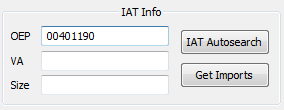
Then single step into the jump by pressing F7. This will take us to the OEP of the packed binary.

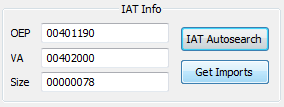
We get 00401190 as our OEP. We can now dump the unpacked file starting from its OEP and fix the IAT. Let’s do this by clicking the “S” button to use the Scylla plugin in x32dbg:
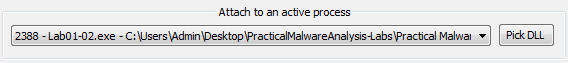
Then we have to select our active process:
And change the OEP to 00401190:
Then click “IAT Autosearch” to scan for Imports and press “Yes” when asked for advanced results.
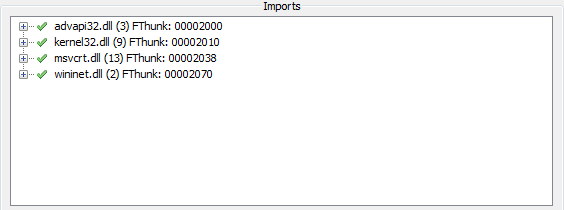
We can now click on “Get Imports” to list all the imports found:
Then click on “Dump” to dump the extracted binary:
After dumping the extracted binary, we have to click “Fix Dump” and load the dumped binary to fix its IAT. This will leave us with a file named “Lab01-02_dump_SCY.exe”. This is the final unpacked binary!
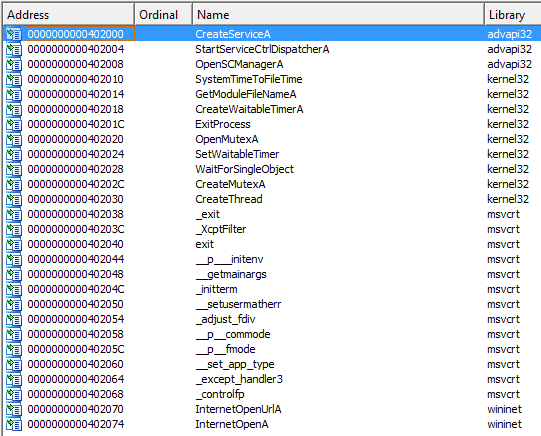
3. Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Answer: In the unpacked sample, we can see that it imports ADVAPI32.dll, KERNEL32.dll, MSVCRT.dll, and WININET.dll. Below is an overview of all imported functions used by the program:
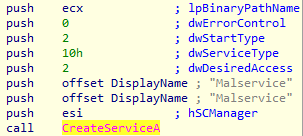
ADVAPI32.dll provides access to advanced core Windows components such as the Service Manager and Registry. In IDA we can see that the CreateServiceA function of ADVAPI32.dll is used to create a new “Malservice”:
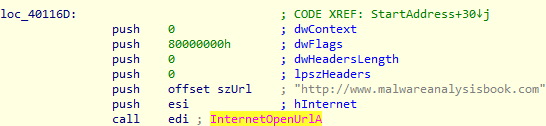
Another interesting import is WININET.dll, as this contains higher-level networking functions that implement protocols such as FTP, HTTP, and NTP. We can see that the InternetOpenUrlA and InternetOpenA functions are imported. InternetOpenUrlA is used to open the http://www.malwareanalysisbook.com URL.
These functions appear to be the most interesting ones in this sample.
4. What host- or network-based indicators could be used to identify this malware on infected machines?
Answer: The Malservice service that is being created can be used as a host-based indicator. The http://www.malwareanalysisbook.com URL that is being opened can be used as a network-based indicator.
Comparing my answers to the Lab 1-2 solutions
Conclusions after comparison:
- My answers were very similar to the lab solutions in the book. The only big difference is that the book provides a slightly easier method for unpacking the malware, which is downloading UPX and running the
upx -o newFilename -d originalFilenamecommand.
Lab 1-3
Analyze the file Lab01-03.exe.
1. Upload the Lab01-03.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
Answer: Lab01-03.exe (SHA256: 7983a582939924c70e3da2da80fd3352ebc90de7b8c4c427d484ff4f050f0aec) is detected by 65 out of 71 security vendors as malicious at the time of writing.
2. Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Answer: If we view Lab01-03.exe in PEiD, we can see that it is packed with FSG 1.0 -> dulek/xt:
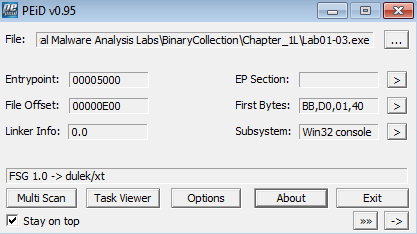
The Virtual Size of the PE section headers are also larger than the Size of Raw Data, and the only imports found are LoadLibraryA and GetProcAddress:
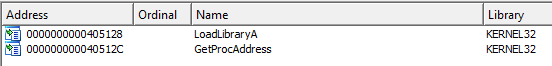
Programs packed with FSG are a lot harder to unpack than UPX (previous sample). I did not manage to unpack the sample at the time of writing, and will return to it once I become more familiar with manual unpacking.
3. Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Answer: I will return to this question after completing Chapter 18: Packers and Unpacking.
4. What host- or network-based indicators could be used to identify this malware on infected machines?
Answer: I will return to this question after completing Chapter 18: Packers and Unpacking.
Comparing my answers to the Lab 1-3 solutions
Conclusions after comparison:
- The book mentions that we cannot unpack this sample at this moment, as the skills to do so have not been covered yet. This file will be analyzed again in Chapter 18.
Lab 1-4
Analyze the file Lab01-04.exe.
1. Upload the Lab01-04.exe file to http://www.VirusTotal.com/. Does it match any existing antivirus definitions?
Answer: Lab01-04.exe (SHA256: 0fa1498340fca6c562cfa389ad3e93395f44c72fd128d7ba08579a69aaf3b126) is detected by 60 out of 71 security vendors as malicious at the time of writing.
2. Are there any indications that this file is packed or obfuscated? If so, what are these indicators? If the file is packed, unpack it if possible.
Answer: The file does not appear to be packed or obfuscated. All PE section headers are visible and the Virtual Size of the headers are never larger than the Size of Raw Data. PEiD tells us that the program was compiled with Microsoft Visual C++ 6.0. There are 34 imported functions, of which LoadLibraryA and GetProcAddress are 2, but with all of the other information gathered I would say that this program is not packed or obfuscated.
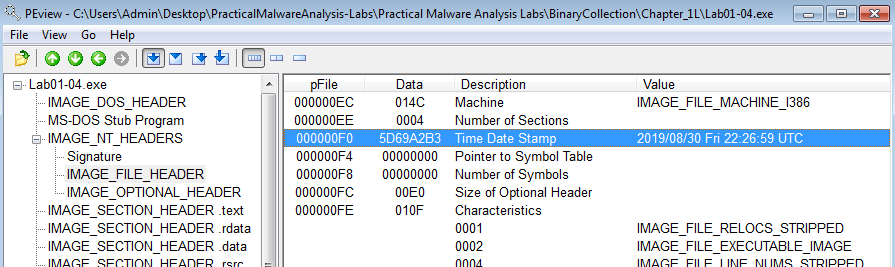
3. When was this program compiled?
Answer: Lab01-04.exe was compiled on 30 August 2019 at 22:26:59 UTC.
4. Do any imports hint at this program’s functionality? If so, which imports are they and what do they tell you?
Answer: Below is a complete list of imports that the program uses:
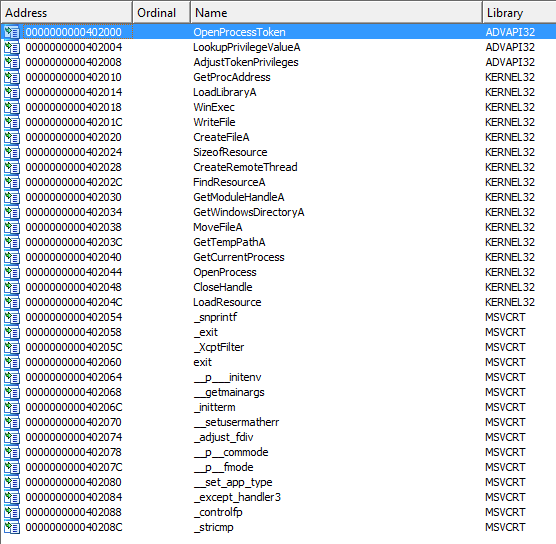
Out of these imports, I would say that WinExec, WriteFile, and CreateFileA are the most interesting functions. These functions could be used to create a new file and run it.
5. What host- or network-based indicators could be used to identify this malware on infected machines?
Answer: Running strings by Sysinternals on the program reveals the following interesting strings: \winup.exe, \system32\wupdmgrd.exe, http://www.practicalmalwareanalysis.com/updater.exe
The first two executables could be used as a host-based indicator and the URL could be used as a network-based indicator.
6. This file has one resource in the resource section. Use Resource Hacker to examine that resource, and then use it to extract the resource. What can you learn from the resource?
Answer: After opening the file in resource hacker, we can see the 4D 5A file signature. This indicates that another executable is being loaded.
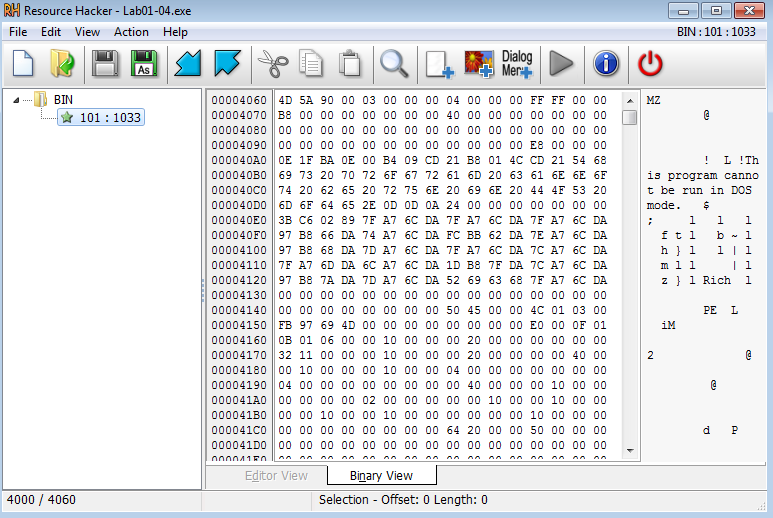
We can simply save this executable to further analyze it.
Let’s have a look at the imports of this file:
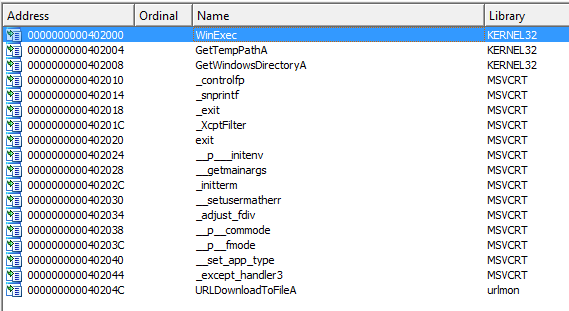
It looks like this is some kind of downloader that runs another malicious program. The URLDownloadToFileA and WinExec functons are being used in order to do so. If we have a look at the strings of this program, we can see another call to http://www.practicalmalwareanalysis.com/updater.exe.
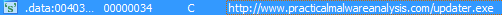
Comparing my answers to the Lab 1-4 solutions
Conclusions after comparison:
- The compile time of Lab01-04.exe is faked. The program could not have been compiled in August 2019, as the Practical Malware Analysis book was not released at that time yet.
- The imports from advapi32.dll tell us that the program does something with permissions, and we can assume that it tries to access protected files using special permissions.
- The LoadResource, FindResource, and SizeOfResource functions tell us that the program loads data from the resource section.