Practical Malware Analysis - Lab 11 write-up

Chapter 11 - “Malware Behavior” is the first chapter of part 4 in the Practical Malware Analysis book. Part 4 is all about malware functionality. Chapter 11 discusses malware types such as backdoors and credential stealers, persistence mechanisms like DLL hijacking, privilege escalation using SeDebugPrivilege, and user-mode rootkit techniques.
Lab 11-1
Analyze the malware found in Lab11-01.exe.
1. What does the malware drop to disk?
Answer: Procmon results show that the malware drops a file named msgina32.dll in the current directory.
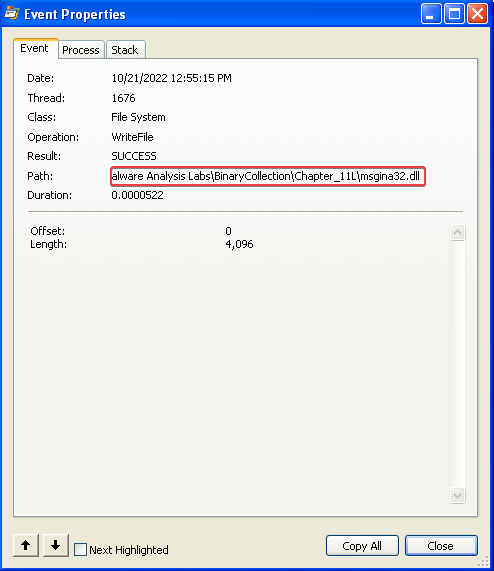
During basic static analysis on the Lab11-01.exe file, I noticed that there’s another executable in the .rsrc section of the program:
Exporting this resource and comparing the file hash to the msgina32.dll file shows us that this is the same file.
2. How does the malware achieve persistence?
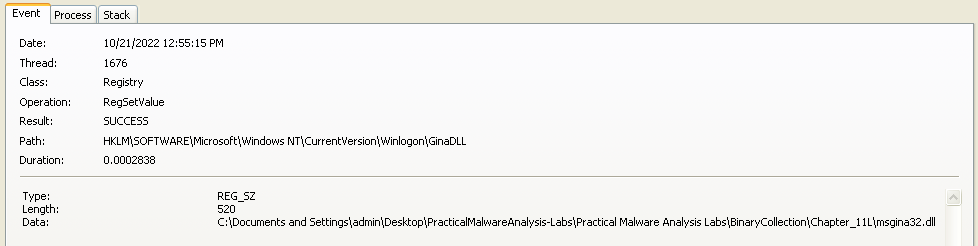
Answer: The program creates a new registry key named HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GinaDLL with a value that points to the location of the malicious msgina32.dll file.
3. How does the malware steal user credentials?
Answer: This malware uses GINA interception to steal user credentials. GINA interception is a credential stealing technique on Windows XP. The GINA system was intended to allow legitimate third parties to customize the logon process by adding support for things like authentication with RFID tokens.
Windows provides the HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GinaDLL registry key location where third-party DLLs will be found and loaded by Winlogon. In my previous answer we already saw that the location to the malicious msgina32.dll file is placed here.
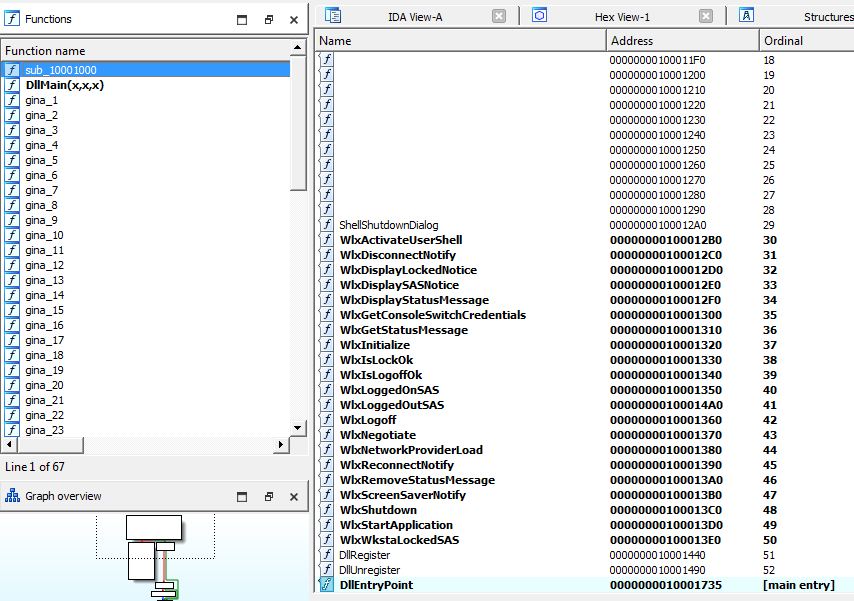
The book mentions that in order to intercept communication between Winlogon and the legitimate msgina.dll, the malware must contain all DLL exports required by GINA. It must export more than 15 functions, most of which are prepended with Wlx. If you are analysing a DLL with many export functions that begin with the string Wlx, you have a good indicator that you are examining a GINA interceptor. That is exactly what we see when we look at the export table of the malicious msgina32.dll file.
4. What does the malware do with stolen credentials?
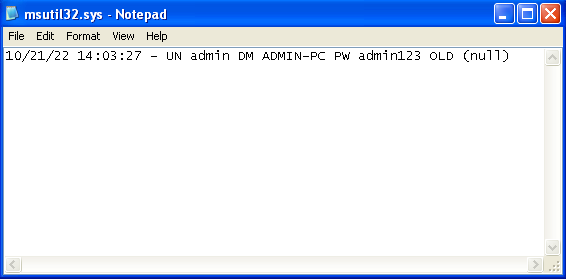
Answer: The stolen credentials are stored in a file called msutil32.sys, which can be found in C:\WINDOWS\system32.
The WlxLoggedOutSAS export function of the malicious msgina32.dll file contains the following instructions:
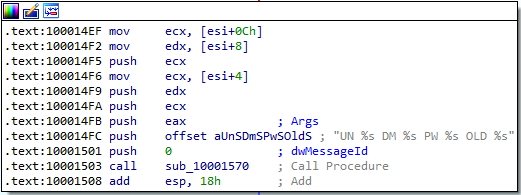
It takes parameters of the credential information and a format string to print credentials (that looks a lot similar to the example described in the book) before calling the sub_10001570 function.
The sub_10001570 function contains the name of the file that the credentials will be written to:
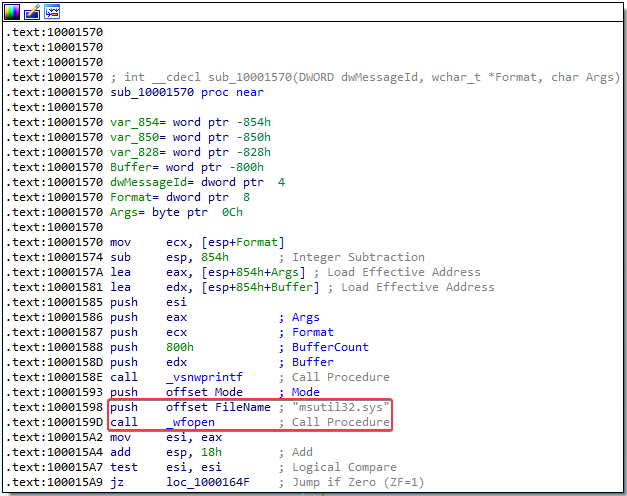
5. How can you use this malware to get user credentials from your test environment?
Answer: You can open the msutil32.sys file in notepad to view the credentials after rebooting and logging in:
Comparing my answers to the Lab 11-1 solutions
Conclusions after comparison:
- No differences! w00t!
Lab 11-2
Analyze the malware found in Lab11-02.dll. Assume that a suspicious file named Lab11-02.ini was also found with this malware.
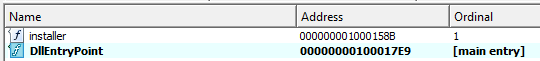
1. What are the exports for this DLL malware?
Answer: installer and DllEntryPoint.
2. What happens after you attempt to install this malware using rundll32.exe?
Answer: You can install the malware by supplying it with the installer export. The command to install the malware is: rundll32 Lab11-02.dll, installer.
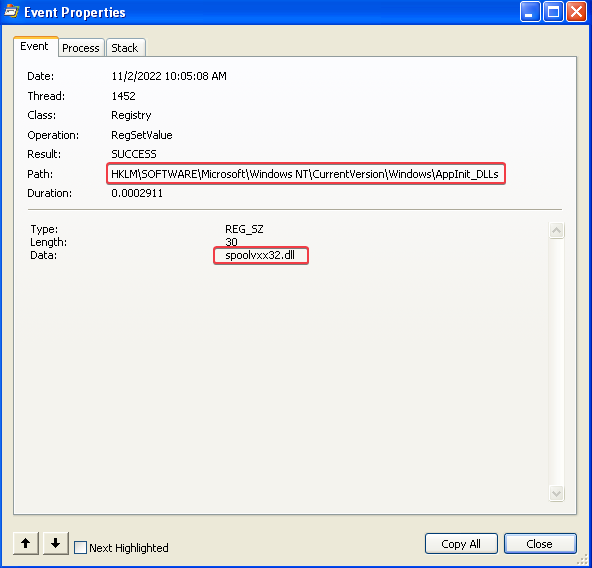
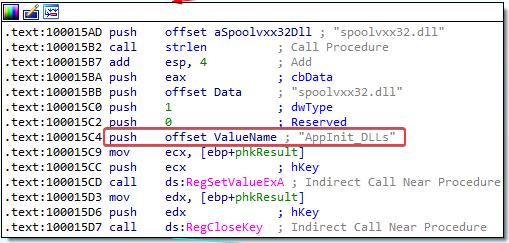
Filtering on “rundll32.exe” in procmon shows that the installer adds spoolvxx32.dll to the HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs registry key:
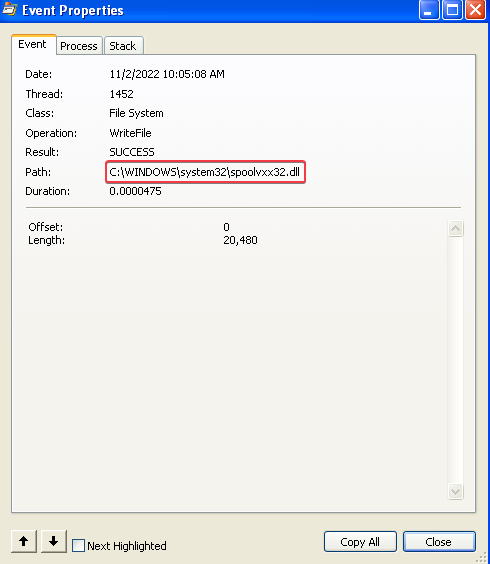
The spoolvxx32.dll file is created in C:\WINDOWS\system32:
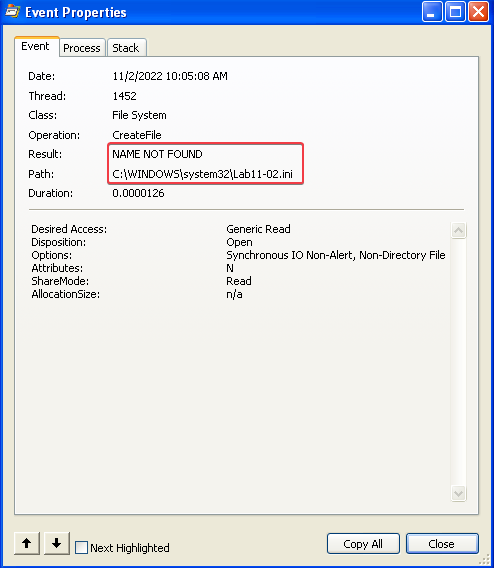
3. Where must Lab11-02.ini reside in order for the malware to install properly?
Answer: The installer attempts to read the Lab11-02.ini file from the C:\WINDOWS\system32 directory. This is where the file should reside in order for the malware to install properly.
4. How is this malware installed for persistence?
Answer: The malware uses the HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs registry key to achieve persistence. The spoolvxx32.dll file is added to the string of DLLs. AppInit_DLLs are loaded into every process that loads User32.dll. Most processes load User32.dll, and those processes will now also load the malicious spoolvxx32.dll file.
5. What user-space rootkit technique does this malware employ?
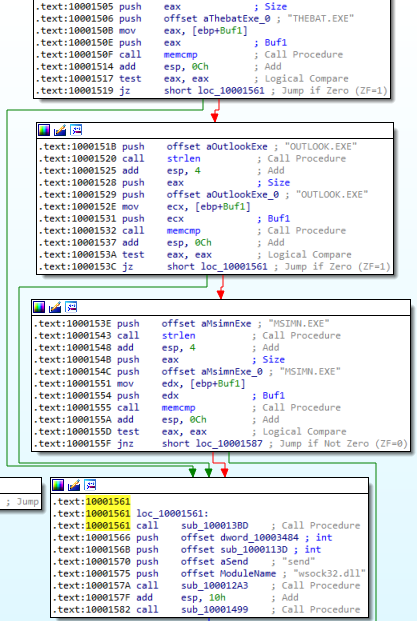
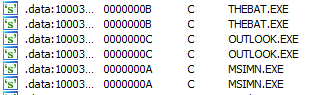
Answer: This malware performs an inline hook on the send function of wsock32.dll if the e-mail clients THEBAT.EXE, OUTLOOK.EXE, or MSIMN.EXE are used:
6. What does the hooking code do?
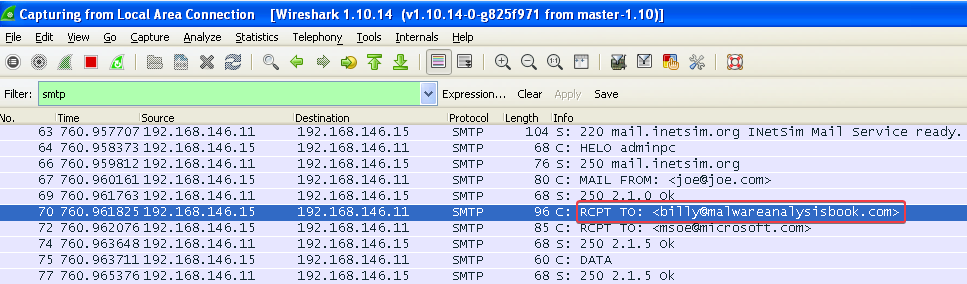
Answer: After playing around with Outlook Express and a fake mail server using INetSim, we can see that the hooking code adds another recipient to any e-mail sent by the victim:
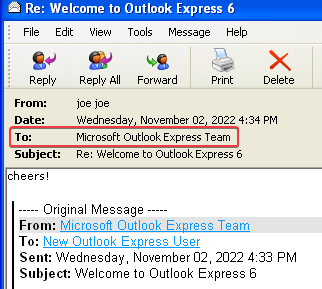
The additional [email protected] recipient cannot be seen when the victim views their sent items:
7. Which process(es) does this malware attack and why?
Answer: THEBAT.EXE, OUTLOOK.EXE, and MSIMN.EXE. These are mail clients that the malware targets.
8. What is the significance of the .ini file?
Answer: I couldn’t figure out what the significance of the .ini file is. It appears to be random encoded data:
9. How can you dynamically capture this malware’s activity with Wireshark?
Answer: As already shown in answer 6, you can filter on SMTP traffic to capture the malware’s activity.
Comparing my answers to the Lab 11-2 solutions
Conclusions after comparison:
- The .ini file contains the encoded
[email protected]address that we discovered before. The function that is responsible for decoding this address is the first function called after opening a handle to the .ini file. We could’ve confirmed that this is a decoding function by loading the DLL in OllyDbg and placing a breakpoint at0x100016CA.
Lab 11-3
Analyze the malware found in Lab11-03.exe and Lab11-03.dll. Make sure that both files are in the same directory during analysis.
1. What interesting analysis leads can you discover using basic static analysis?
Answer: Using only basic static analysis, we can see that the Lab11-03.exe program copies the Lab11-03.dll file into C:\WINDOWS\System32\inet_epar32.dll. It also starts a service called cisvc.
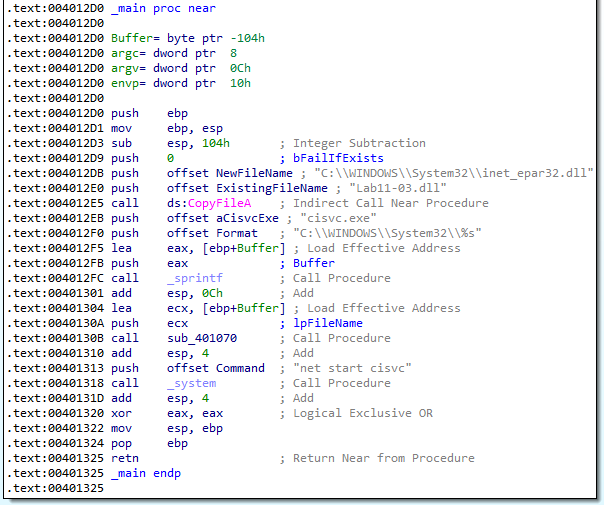
Imports table of Lab11-03.dll shows that it may contain keylogger functionality:
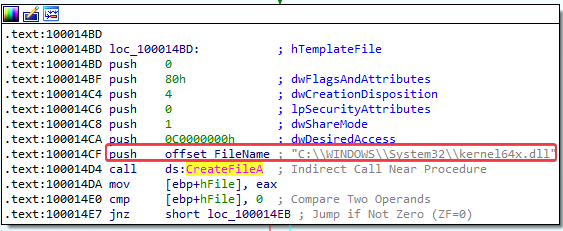
Lab11-03.dll also seems to create a new DLL file called C:\WINDOWS\System32\kernel64x.dll:
2. What happens when you run this malware?
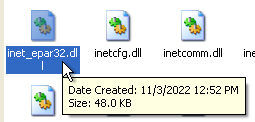
Answer: We confirm that the malware creates C:\WINDOWS\System32\inet_epar32.dll, which we can see is a copy of Lab11-03.dll after checking the file hashes.
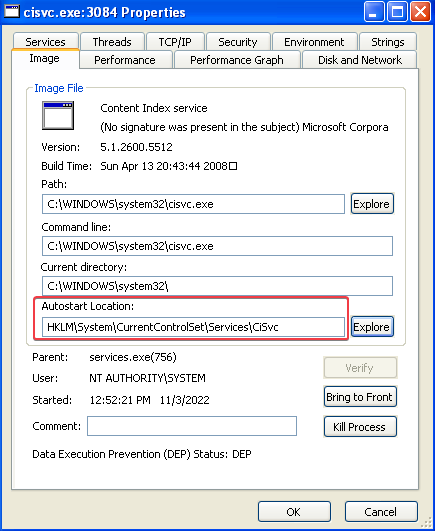
The malware also launches C:\WINDOWS\System32\cisvc.exe, which is installed as a service named Content Index Service:
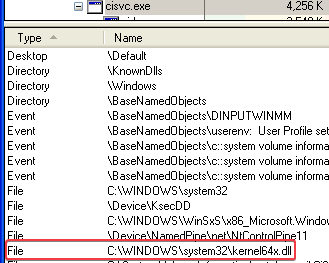
The cisvc.exe process has a file handle to C:\WINDOWS\system32\kernel64x.dll, which we also saw being referred to by the Lab11-03.dll file in our answer to question 1.
It looks like this file is used to store keylogs. If we open kernel64x.dll in notepad we see a bunch of entries related to windows that we opened, along with hexadecimal data (possibly keystrokes):
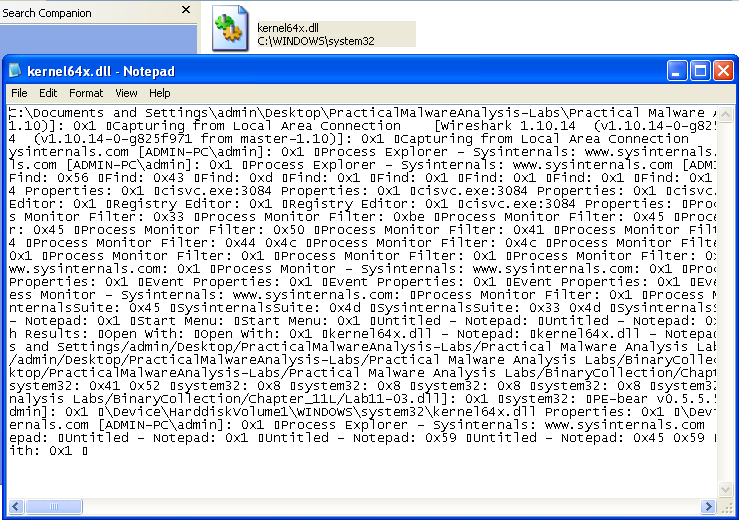
3. How does Lab11-03.exe persistently install Lab11-03.dll?
Answer: cisvc.exe is modified so that it loads the malicious inet_epar32.dll file, which is a copy of Lab11-03.dll.
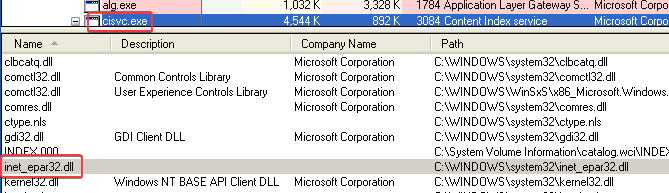
4. Which Windows system file does the malware infect?
Answer: cisvc.exe
5. What does Lab11-03.dll do?
Answer: Lab11-03.dll creates a mutex called MZ:
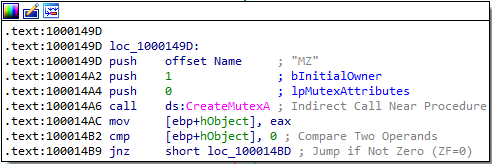
It then creates a file named kernel64x.dll:
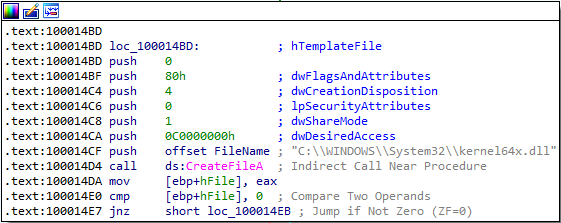
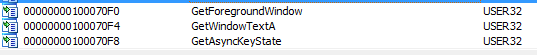
After getting a file pointer to kernel64x.dll, the program stays in a loop with calls to GetForegroundWindow, GetWindowTextA, GetAsyncKeyState, and WriteFile. This means that Lab11-03.dll is most likely a polling keylogger. As discussed in the book, polling uses the Windows API to constantly poll the state of the keys, typically using the GetAsyncKeyState and GetForegroundWindow functions.
6. Where does the malware store the data it collects?
Answer: The keylogs are stored in kernel64x.dll.
Comparing my answers to the Lab 11-3 solutions
Conclusions after comparison:
- The malware persistently installs
Lab11-03.dllby trojanizing the indexing service by entry-point redirection. It redirects the entry point ofcisvc.exeto loadinet_epar32.dlland call its exportzzz69806582.