Practical Malware Analysis - Lab 3 write-up

Chapter 3 of the Practical Malware Analysis book is the second chapter to contain lab assignments. Chapter 3 is all about basic dynamic analysis, and is described in the book as any examination performed after executing malware. Dynamic malware analysis lets you observe the malware’s true functionality.
For the launch environment, I will be using the following tools:
- Process Monitor (procmon)
- Process Explorer
- RegShot
- INetSim (installed on REMnux VM)
- ApateDNS
- Wireshark
These tools are recommended by the author when performing basic dynamic analysis. Let’s dive in!
Lab 3-1
Analyze the malware found in the file Lab03-01.exe using basic dynamic analysis tools.
1. What are this malware’s imports and strings?
Answer: This malware has only one import: the ExitProcess function of the kernel32.dll library.

If we look at the strings, we can see some other potential libraries being used by the program, such as ntdll.dll, user32.dll, and advpack.dll.
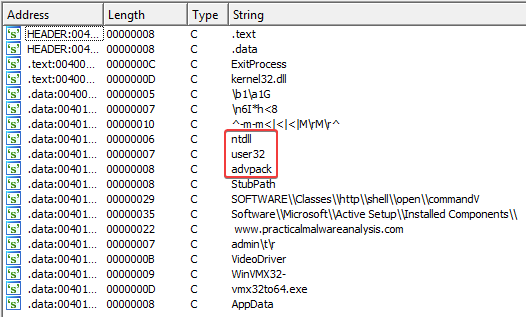
Another interesting string is Software\\Microsoft\\Active Setup\\Installed Components\\. This string is a registry entry that is related to Active Setup, a mechanism for executing commands once per user early during logon. It looks like this mechanism is being used to make the malware more persistant. After reading the Active Setup Explained blog post by Helge Klein, I learned that the StubPath string contains the command that is being executed if Active Setup determines this component needs to run during logon. An example Active Setup component that runs notepad once per user could look like this:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\MyComponent]
@="My Active Setup Component"
"StubPath"="notepad"
In the case of this malware, my guess is that the StubPath contains vmx32tox64.exe to run this file during logon.
When we run the malware on our dynamic analysis VM, we can see some more strings in Process Explorer:
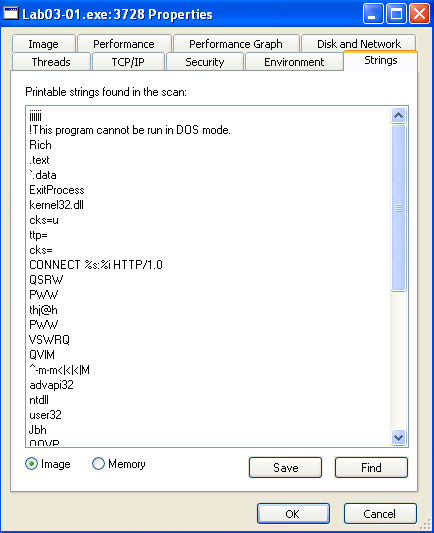
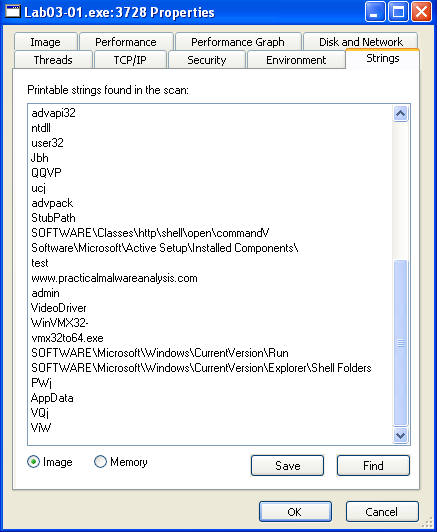
Here’s a full list of the strings that I found interesting:
CONNECT %s:%i HTTP/1.0ntdlluser32advpackStubPathSOFTWARE\Classes\http\shell\open\commandVSoftware\Microsoft\Active Setup\Installed Components\www.practicalmalwareanalysis.comvmx32to64.exeSOFTWARE\Microsoft\Windows\CurrentVersion\RunSOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
2. What are the malware’s host-based indicators?
Answer: To gather the host-based indicators, I’ve set up the following simple procmon filter:
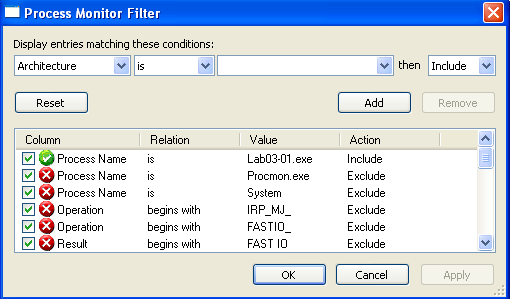
After running the malware and investigating the events in procmon, we can see that a file called vmx32to64.exe gets created in C:\WINDOWS\system32\. This is our first host-based indicator:
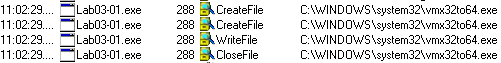
This file has the same hash as Lab03-01.exe.
A second host-based indicator that we can see in procmon is the HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\VideoDriver registry key that is being set:
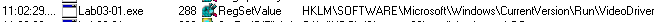
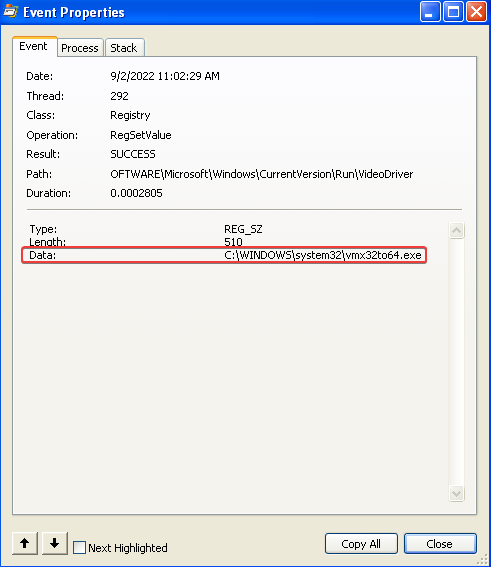
This registry contains the path to the vmx32to64.exe file that was created earlier, possibly as a persistence mechanism:
The third host-based indicator that I found is the mutex named WinVMX32 that I found in Process Explorer after examining the Handles view:
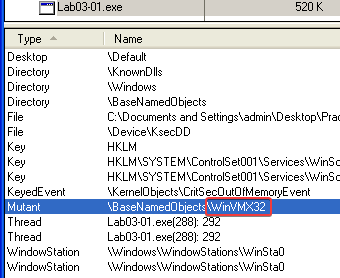
3. Are there any useful network-based signatures for this malware? If so, what are they?
Answer: After reviewing the ApateDNS results, we can see multiple requests to www.practicalmalwareanalysis.com. We also saw this URL while looking at the strings. This URL could be used as a network-based signature.
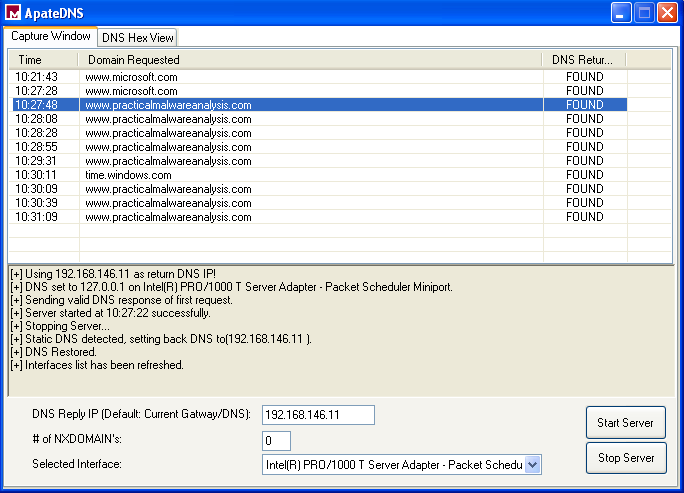
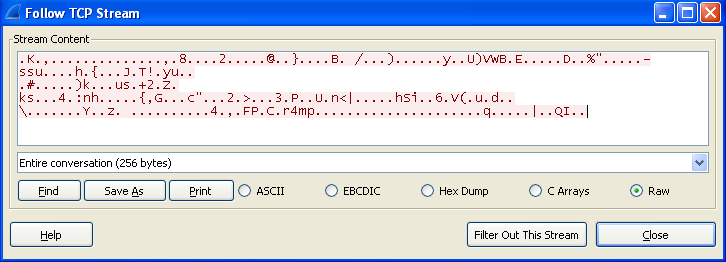
Reviewing the TCP streams in Wireshark shows random ASCII data, which is often indicative of a custom protocol. The skills required to draft a network-based signature from this will be explored in Chapter 14 of the book.
Comparing my answers to the Lab 3-1 solutions
Conclusions after comparison:
- My answers were very similar to the solutions included in the book. There’s just one thing that we missed: by further reviewing the data in Wireshark, we can see that the malware appears to beacon out over port 443. The beacon packets are of consistent size (256 bytes) and appear to contain random data not related to the SSL protocol that normaly operates over port 443.
Lab 3-2
Analyze the malware found in the file Lab03-02.dll using basic dynamic analysis tools.
1. How can you get this malware to install itself?
Answer: After inspecting the .dll file in Dependency Walker, we can see the following exported functions:
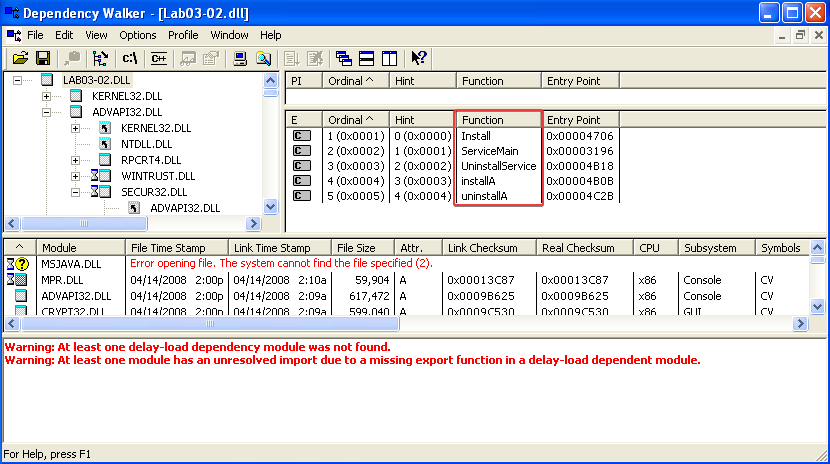
The presence of the exported function called ServiceMain indicates that the malware runs as part of a service. However, we have to keep in mind that the names of exported functions can be changed by the author. Thus, the author of this malware could be misleading us with this function name.
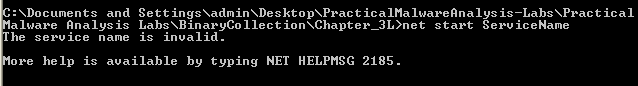
Since there are some references to a service in the exported functions, I would first try to get the malware to install itself by running the following command: rundll32 Lab03-02.dll, Install ServiceName.
When trying to start the service, we unfortunately get an error that the service name is invalid:
I next tried to install the malware by using the installA export argument. The rundll32 Lab03-02.dll, installA command ran successfully! After comparing my Regshot results I noticed that the malware added some interesting registry entries:
Interesting registry keys added after running the Lab03-02.dll with the installA export argument:
HKLM\SYSTEM\ControlSet001\Services\IPRIP
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Parameters
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Security
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Parameters
HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Security
So, we now know that this DLL actually creates a new service! The new service is called IPRIP. Here’s a view of the service in regedit:
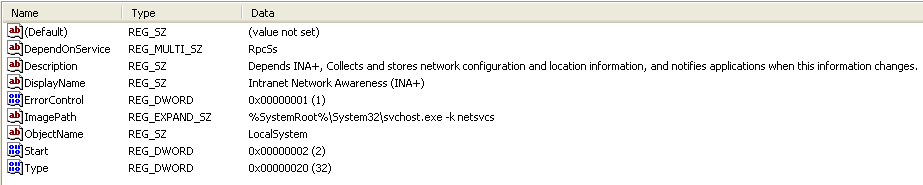
2. How would you get this malware to run after installation?
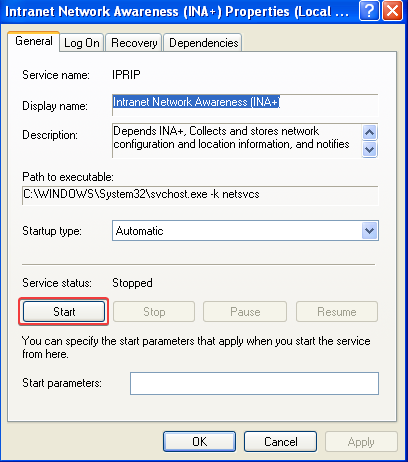
Answer: We can get the malware to run by starting the service. This can be done with the following command: net start IPRIP
We can also start the service from the GUI. If you open services.msc you will find the service under the name “Intranet Network Awareness (INA+)”, as seen in the registry entry in our previous answer.
3. How can you find the process under which this malware is running?
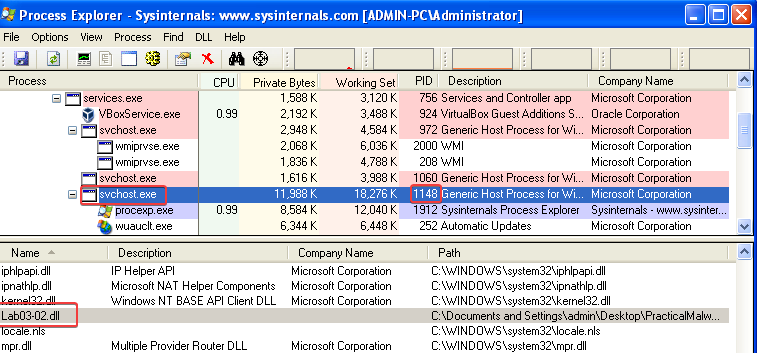
Answer: After launching the malware with net start IPRIP, I looked for the svchost.exe process entries in Process Explorer. The reason for this is that the IPRIP service uses svchost.exe in their path to executable (ImagePath). I then enabled the DLLs lower pane view and looked for the svchost.exe entry that was using Lab03-02.dll. This process has a PID of 1148.
4. Which filters could you set in order to use procmon to glean information?
Answer: We can filter on the PID 1148 that we just found.
5. What are the malware’s host-based indicators?
Answer: For the host-based indicators, the registry keys related to the IPRIP service are important. The display name of this service, “Intranet Network Awareness (INA+)” can also be used as a host-based indicator. After launching the IPRIP service, some additional registry keys were added. These can be found in HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_IPRIP and HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_IPRIP.
6. Are there any useful network-based signatures for this malware?
Answer: In our ApateDNS results we see a connection attempt to the practicalmalwareanalysis.com URL. This can be used as a network-based signature.
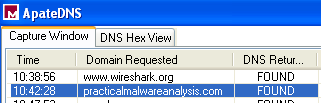
If we investigate our INetSim logs on the REMnux VM, we can see that a GET request was made to serve.html:
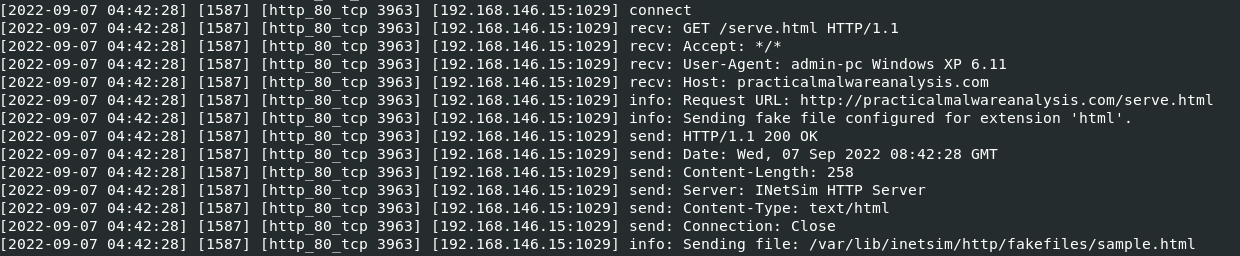
Comparing my answers to the Lab 3-2 solutions
Conclusions after comparison:
- For question 3: Could have also used the Find DLL feature of Process Explorer to search for Lab03-02.dll, instead of going through the list of DLLs for every svchost.exe instance.
- For question 6: We could have included the “Windows XP 6.11” part of the User-Agent as a network signature, as this is consistently used through several tests.
Lab 3-3
Execute the malware found in the file Lab03-03.exe while monitoring it using basic dynamic analysis tools in a safe environment.
1. What do you notice when monitoring this malware with Process Explorer?
Answer: After Lab03-03.exe launches, it spawns a new svchost.exe process and then terminates itself. In the properties screen of the spawned svchost.exe we can see that Lab03-03.exe is the parent, but Lab03-03.exe is no longer listed in the process view.
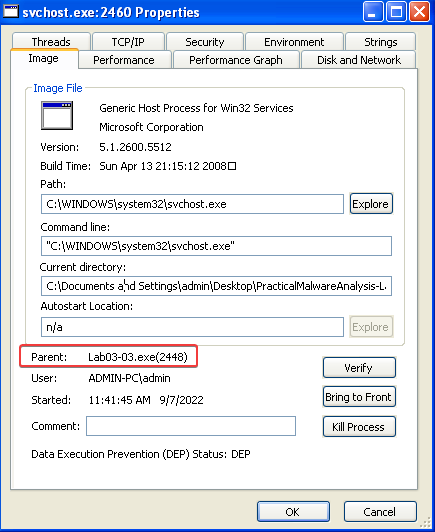
2. Can you identify any live memory modifications?
Answer: Yes, if we open the Strings window and compare the strings of this svchost.exe instance on image (disk) to the strings in memory, we can see clear differences. This indicates that process replacement has occured:
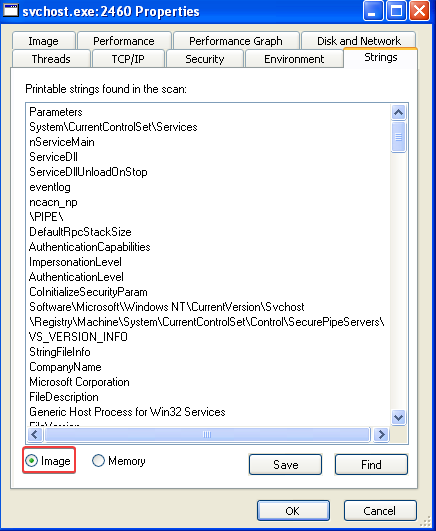
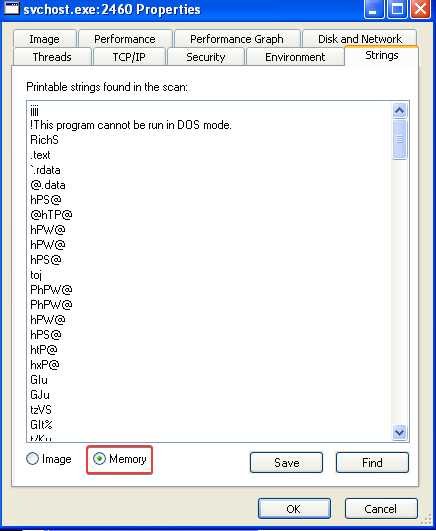
3. What are the malware’s host-based indicators?
Answer: The malware creates a practicalmalwareanalysis.log file in the current directory:
4. What is the purpose of this program?
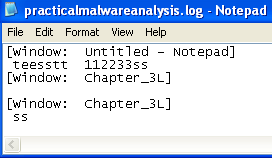
Answer: If we open the log file, we can cleary see that this program is a keylogger:
Comparing my answers to the Lab 3-3 solutions
Conclusions after comparison:
- If we filtered on the PID of the newly created svchost.exe process in procmon, we would have seen
CreateFileandWriteFileevents to thepracticalmalwareanalysis.logfile if we were to type anything.
Lab 3-4
Analyze the malware found in the file Lab03-04.exe using basic dynamic analysis tools. (This program is analyzed further in the Chapter 9 labs.)
1. What happens when you run this file?
Answer: The file deletes itself after execution.
2. What is causing the roadblock in dynamic analysis?
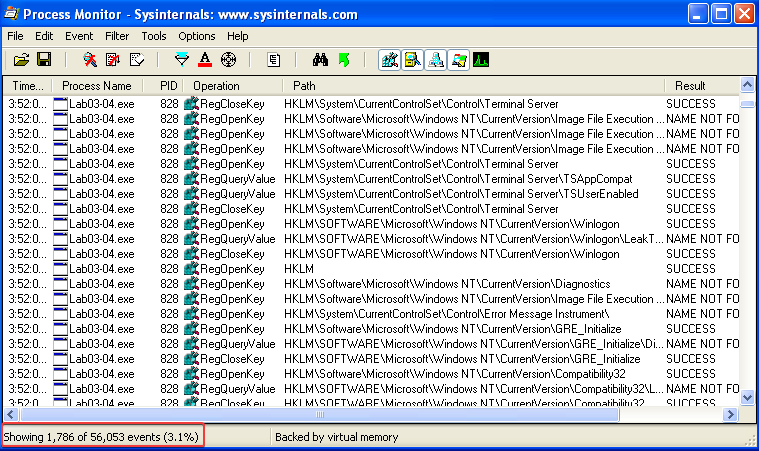
Answer: The program seems to create a lot of noise. When inspecting the filtered results in procmon, we still have over 1500 events created by the Lab03-04.exe process. It seems to open and close a bunch of random registry keys to make dynamic analysis more difficult.
3. Are there other ways to run this program?
Answer: I could not find another way to run this program.
Comparing my answers to the Lab 3-4 solutions
Conclusions after comparison:
- If we viewed the strings of this file, we would see command-line parameters shown (such as
-in,-reand-ce). This indicates that we need to provide a command-line argument in order to launch the malware. Unfortunately, running the program with these options will still result in the program deleting itself. - Basic dynamic techniques are not sufficient for investigating this malware sample. This malware sample will be revisited in the Chapter 9 labs!