Retrospect and future plans - Pt. 3
“new year, new me”
This has been quite an inactive year for my blog so far, but I’m still alive and kicking. Let’s look back on some key moments of the past 8 months and discuss my future plans.
Retrospect: the past eighth months
January 2023 - Passed SRE minor and working part-time
At the start of this year I passed the Software Reversing & Exploitation minor with a whopping 9,7 out of 10 grade. I already wrote a little bit about the structure of this minor in my previous post, but I want to mention again that it was a ton of fun. The minor can be challenging for those that haven’t dipped their toes in the wonderful world of reverse engineering before, but teachers Mike Gilhespy and Daniel Meinsma surely motivated the entire class with their enthusiasm. Personally, I already had some experience with reversing and binary exploitation before the minor, but I still learned a lot from it. I loved the fact that you could come up with your own learning plan for a topic related to the minor, which you were able to spend 16 hours per week on for the full semester. I dedicated all this time to learning more about malware analysis, and documented my progress in the required biweekly “Heroes Journey” reports. Looking back, this minor was one of my (and perhaps even the most) favourite moments of the entire study.
This month, my girlfriend and I also started working as part-time SOC analysts! The first month mainly consisted of trainings.
February 2023 - Graduation internship
February 6th kicked off the start of my graduation internship, for which I examined the technical differences between 2 Android malware families: ERMAC and Hook. I did not have to write a thesis for my graduation, but I did have to give multiple presentations for the examiners and hand in reports at the end of each “phase” of the graduation internship. There were a total of 4 phases, and the final phase consisted of an examination session in which I did have to defend my research and certain professional competencies. As I did not have to write a thesis, I worked on a final product that is quite unique: a blog post to be published on the company’s website.
April 2023 - vroom vroom
After failing my practical driving exam 3 times, I finally passed. In my previous attempts I would get quite nervous at the start and I couldn’t stop thinking about any small mistake that I made during the exam. On my 4th attempt those nerves were long gone: I felt super relaxed, and it went really well! I’m not a huge fan of driving, but I’ll try to keep at it so that I don’t “unlearn” it.

June 2023 - Still blogging
This month marked the end of my graduation internship, and I finished writing my blog post on the technical differences between ERMAC and Hook malware. The blog was teased in the spotlight of the company’s Threat Pulse - a monthly report on what’s happening in TI. This report is shared with customers, and later in a slimmed down version to media outlets. Due to some unforeseen circumstances, the blog hasn’t been released on the main website of the company yet. Hopefully this’ll happen soon!
Here’s a sneak peak of the blog:
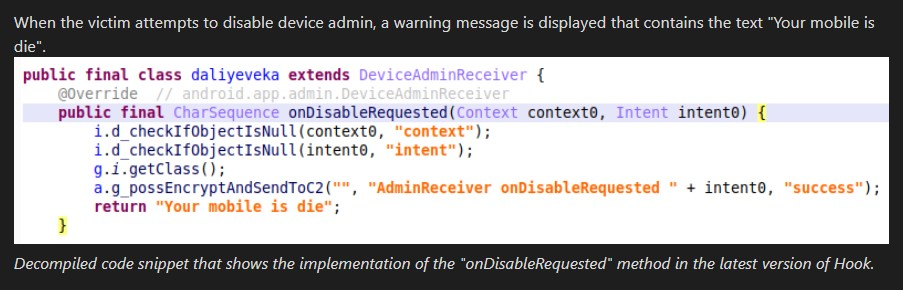
July 2023 - A dream come true
I started working as a (Junior) Malware Analyst this month, which is a dream come true for me! In my previous post I mentioned that they would reserve this position for me if the internship went well, and it actually happened. I think it’s awesome that one of my hobbies is now also my full-time job, and I’m grateful for getting the opportunity to work with the amazing people in my team.
Future plans
Malware analyst, now what?
Now that my dream of working as a malware analyst has come true, I hope to stay in this role for a long time. I’m still a junior at the time of writing, and I’m aware of the fact that I have much to learn when comparing my skills to some of the wizards in my team ;).
Thus, I’d like to focus on further developing my malware analysis skills. Recently, I became a middle tier patron of OALabs (https://www.patreon.com/oalabs/). I’ve been watching OALabs streams for a long time, and it’s nice to be able to watch them back on demand at any time. The middle tier Patreon subscription also comes with exclusive reversing tutorials, which I’m currently going through in order to refresh and further develop my skills. I also have access to some malware analysis related courses that I plan to go through soon, such as Zero2Automated (https://courses.zero2auto.com/). Next to OALabs Patreon material and malware analysis courses, I want to finish reading The IDA Pro Book (https://nostarch.com/idapro2.htm), and reverse samples in my spare time (which I’m also doing during my day-to-day job of course).
Besides further developing my own skills, I’ll also be teaching a co-worker how to analyse mobile malware. I have learned a lot about Android malware during my graduation internship, and I think it’s fun to transfer this knowledge to others. Explaining such subjects will also help my personal understanding of the matter, so everybody wins!